Thousands of n8n systems worldwide have been affected by a critical vulnerability, allowing attackers to execute code.
A critical security flaw has been discovered in the workflow automation platform n8n that could allow attackers to execute arbitrary code. The vulnerability poses a serious risk to organizations using the platform to automate business processes.
Execute code via workflows
The vulnerability (CVE-2025-68613) has a CVSS score of 9.9 out of 10 and was discovered by a security researcher. According to the administrators of the n8n package, code or an instruction entered by a logged-in user when setting up a workflow can be executed in an environment that is not properly shielded. As a result, that input can gain more access than intended to the system on which the software runs. An attacker can then execute code with the same rights as the n8n process itself.
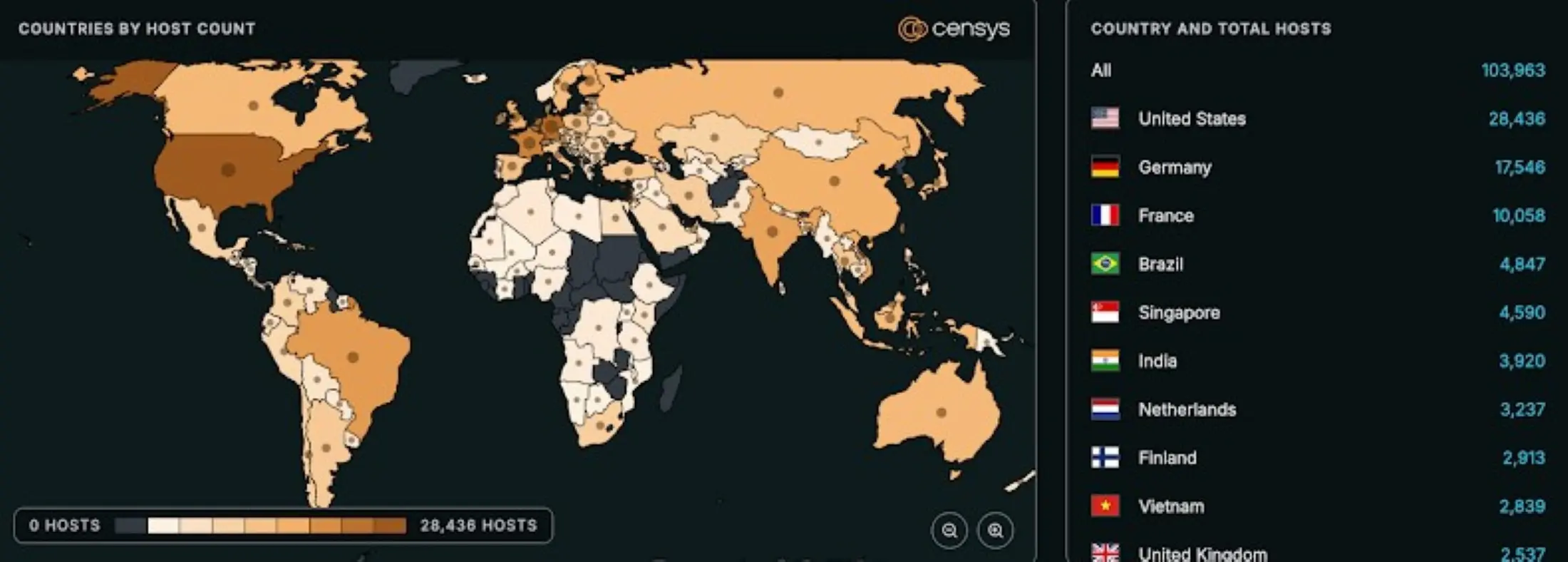
The vulnerability affects all versions from 0.211.0 up to and including 1.120.3. Meanwhile, the problem has been resolved in versions 1.120.4, 1.121.1 and 1.122.0. According to data from Censys, more than 103,000 n8n environments were potentially vulnerable at the end of December, with the largest number in the United States (28,000), Germany (17,651) and France (10,150).
Patching recommended
n8n users are strongly advised to upgrade to a patched version as soon as possible. Those who cannot update immediately should restrict the creation and editing of workflows to strictly trusted users. It also helps to run n8n in an extra shielded environment with limited system rights and network access.
