This contribution was submitted by Fabien A. P. Petitcolas of Smals. Because of the relevant perspective and topicality of the topic, the editors are publishing it in full on ITdaily.
Physical certificates, such as a driver’s license, university degrees, the European Health Insurance Card (EHIC), or the A1 certificate for working abroad (PD A1), and more generally important “paper” documents, have several drawbacks. They are subject to loss, theft, damage or unauthorized duplication, and they do not easily provide the ability to minimize data as required by the European Union’s General Data Protection Regulation (GDPR).
Verifiable credentials (VC – “verifiable attestations”) are digital and cryptographically secure versions of physical certificates that can digitally prove something about a person, such as his or her identity, a qualification obtained, a right or specific factual information, while minimizing the information released1.
These verifiable credentials are defined as a set of one or more claims by an issuer. Like physical certificates, these verifiable credentials can include the following:
- Information related to identifying the subject (e.g., person, organization, object) of the verifiable credentials (e.g., name, photo, identification number)
- Information related to attestation issuer (e.g., government, authentic source, municipalities)
- Information related to the type of attestation in question (e.g. insurance card, disability card, passport, identity card)
- Information related to specific characteristics or attributes the issuer states about the data subject (e.g., date of birth, social security entitlement, nationality)
- Evidence of how the verifiable credential was created (e.g., renewal of a previous attestation, physical presence of a citizen in an administrative office)
- Information on restrictions applicable to the verifiable credential (e.g., attestation validity period)
The key players involved in an architecture for verifiable credentials are described in Figure 1 and include:
- Subject: entity about which claims are made (e.g., person, organization, animal, inanimate object).
- Holder: the entity that currently holds the virtual value and presents it to the controller. This can be the data subject, but also another authorized natural or legal person.
- Issuer: entity that claims one or more subjects by creating a verifiable credential based on those claims (e.g., an institution responsible for coordinating Social Security).
- Controller/verifier: an entity that receives verifiable credentials from the holder through submission and provides services and benefits in return2.
- E-purse: entity that stores a holder’s verifiable credentials, including the software that interacts with the ecosystem on the holder’s behalf.
- Verifiable data registry: conceptually an Internet-accessible registry that contains all essential data and metadata that allow other players to interact.
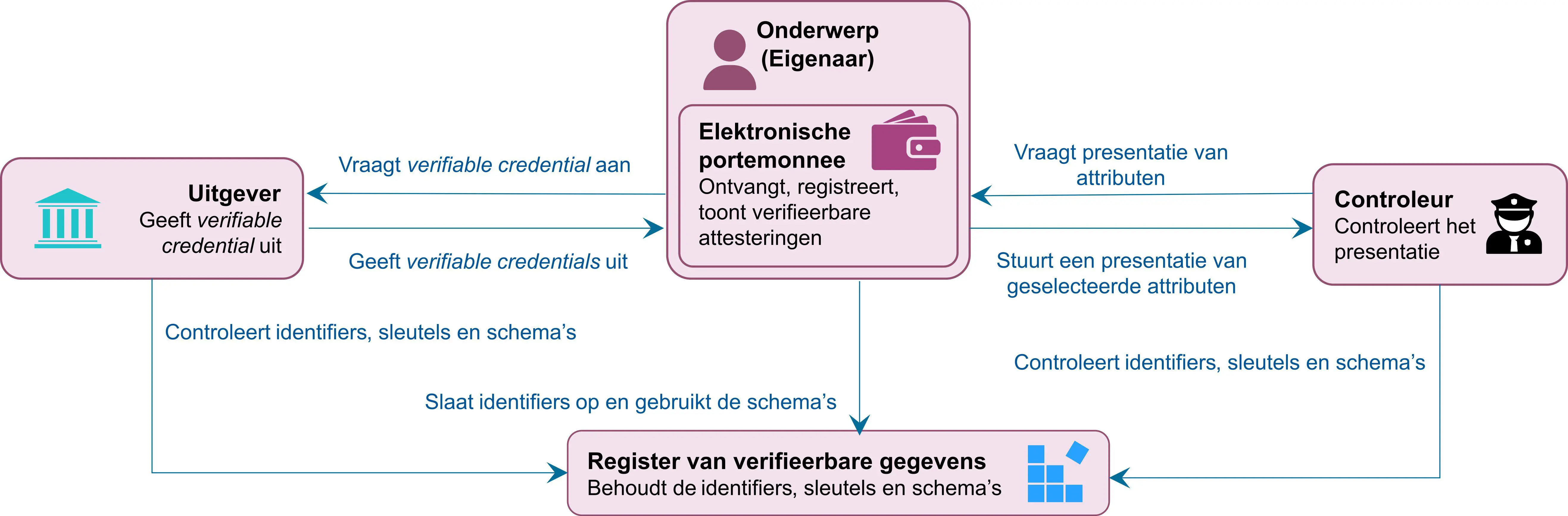
The holder of a verifiable credential can show it to an auditor, who can verify the authenticity of the credential and the identity of the holder. The process of issuing a verifiable credential involves linking an issuer’s claim about a subject to the subject’s identifier using cryptographic evidence. It is this linkage that allows subsets of different attestations to be combined (see below). Once issued, a verifiable credential can be held for an extended period of time and presented for multiple purposes and in multiple ways.
Release of identity attributes
Releasing attributes generally raises confidentiality issues. This is the case in systems where an online identity provider creates on-demand access tokens. In such systems, the identity provider can track the activities of its users or, worse, appropriate their identities. This is also the case in systems that create offline tokens (e.g., X509) because they ask the user to reveal more attributes than strictly necessary and make online transactions linkable to different domains.
The selective disclosure technique (“selective disclosure”) allows holders of verifiable credentials to present only the information they want to show, while keeping the rest of their sensitive data private. This technique is especially useful when a user needs to prove a specific claim but does not want to share all the information on, for example, their ID card.
In the social security coordination context, if a citizen is in a verification situation with a qualified verifier, selective disclosure is not appropriate, as services and benefits may not be provided if only a subset of information is disclosed. In contrast, for non-qualified verifiers (e.g., businesses seeking to verify certain elements of a Social Security document), selective disclosure may be appropriate.
Known cryptographic techniques
Based on zero knowledge proofs (“zero knowledge proof” – ZKP), privacy-preservingattribute-based-credentials or anonymouscredentialshave been proposed as a promising technique for establishing verifiable credentials. Successful implementations of this technique include IBM’s Identity Mixer and Microsoft’s U-Prove. A subset of Idemix’s capabilities has also been used for several years in the Dutch IRMA project. This project has already enabled Dutch citizens to obtain identification information with verified attributes from a number of organizations, including the Dutch Civil Registry.
This technique began to receive more attention in the mid-2010s, with the European ABC4Trust project and also after the emergence of the self-sovereign identity (SSI) concept. Self-sovereign identity is a model of digital identity where a user has techniques to create, verify and (most importantly) possess a digital identity that can be released between trusted parties. This generally means that when a user submits an identity claim to a trusted party, the given identity can be verified without direct intervention by the Identity Provider, which has benefits for the user’s privacy.
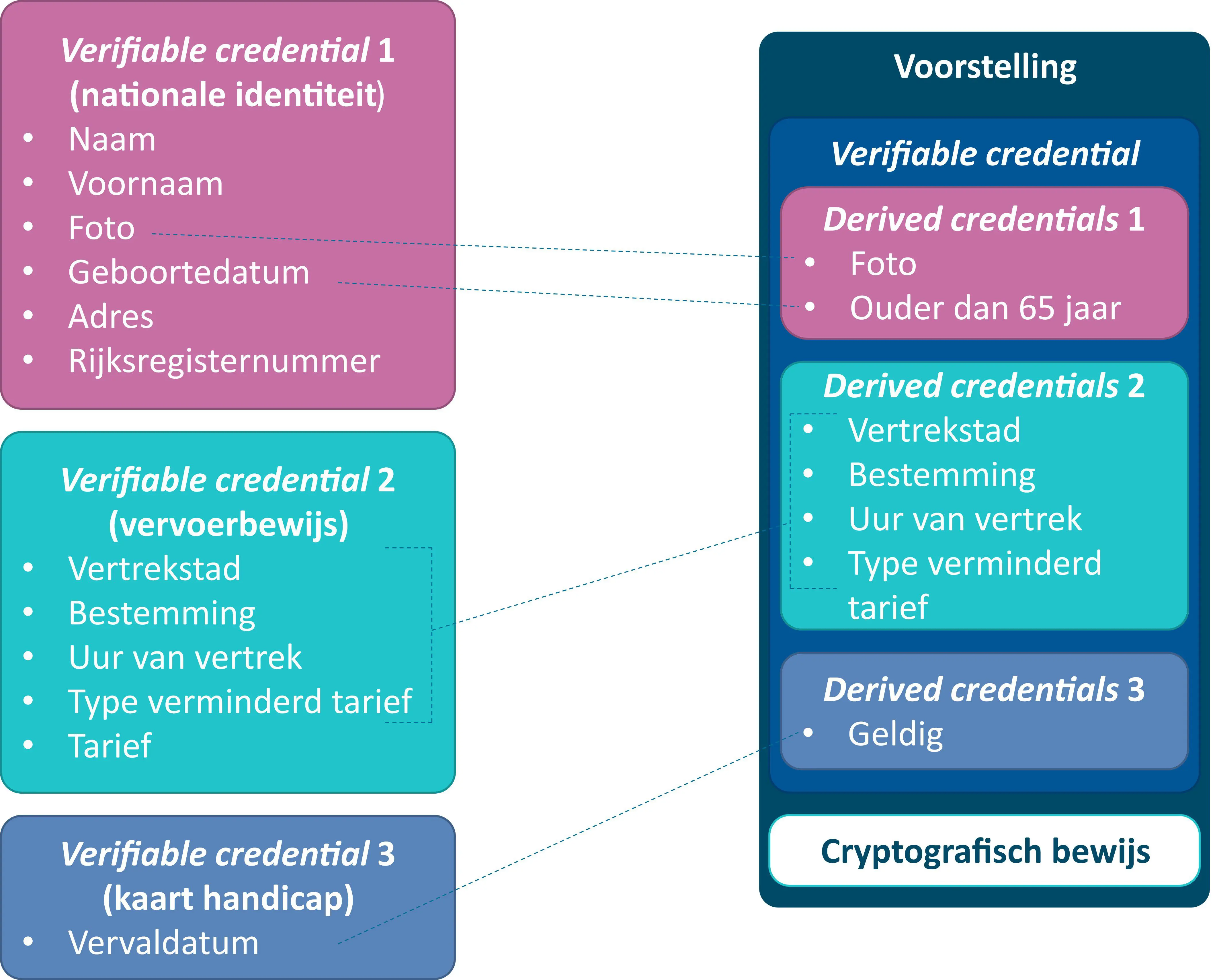
Anonymized attestations can express all the information contained in a physical identity document, with the added advantage that they can be combined (see Figure 2) and reveal only the required attributes (selective disclosure) or even information derived from those attributes. An emblematic example is the date of birth: it is possible to reveal only the age, only the age range (e.g. 50-60 years), or even only the fact that the person is above or below a certain age, etc. without revealing the exact date of birth.
Conclusions
Verifiable credentials, currently being standardized by the World Wide Web Consortium allow physical attestations to be converted into a digital format that can be stored in an electronic wallet such as a European Digital Identity Wallet (EUDIW). Their success depends on a “network effect” that could be brought about by the eIDAS 2.0 regulation (electronic identification and trust services), which is an important step in the development of interoperable digital identities in Europe for both the public and private sectors.
One technique for implementing verifiable credentials is through anonymous attestation, which has been developed since the early 2000s to enable authentication and identification securely and with respect for privacy. The underlying cryptographic techniques – indispensable to the operation of numerous scenarios that rely on verifiable credentials – are well known, but the usability of the resulting technologies for end users, while critical, is still largely unexplored.
This article is an individual contribution of Fabien A. P. Petitcolas, IT Research Consultant at Smals Research. This article was written under his own name and in no way reflects the views of Smals. Interested in working at Smals? Then take a look at the current extensive job offerings.
