A vulnerability in Windows Server Update Services is being actively exploited. Microsoft released an emergency patch on Friday and advises installing it as soon as possible.
The vulnerability CVE-2025-59287 has been known to Microsoft since at least October 14, but active exploits seem to have exploded only since last week. After the security company HawkTrace Security disclosed a proof-of-concept code last Wednesday, organizations like ShadowServer and Eye Security raised alarms about active exploitation. The vulnerability is in Windows Server Update Services (WSUS) for managing updates for Windows systems.
The risk lies in unsafe deserialization by WSUS. During deserialization, a file is converted from a universal data format to the server’s format. This should be a normal process, but deserialization can be
Actively Exploited
Microsoft first reported the vulnerability on October 14, often marking the start of exploitation by cybercriminals. The Dutch cybersecurity company Eye Security reported on Friday that it is aware of a client who was affected. Exploitation is only possible when the WSUS server function is enabled, which is not the default setting.
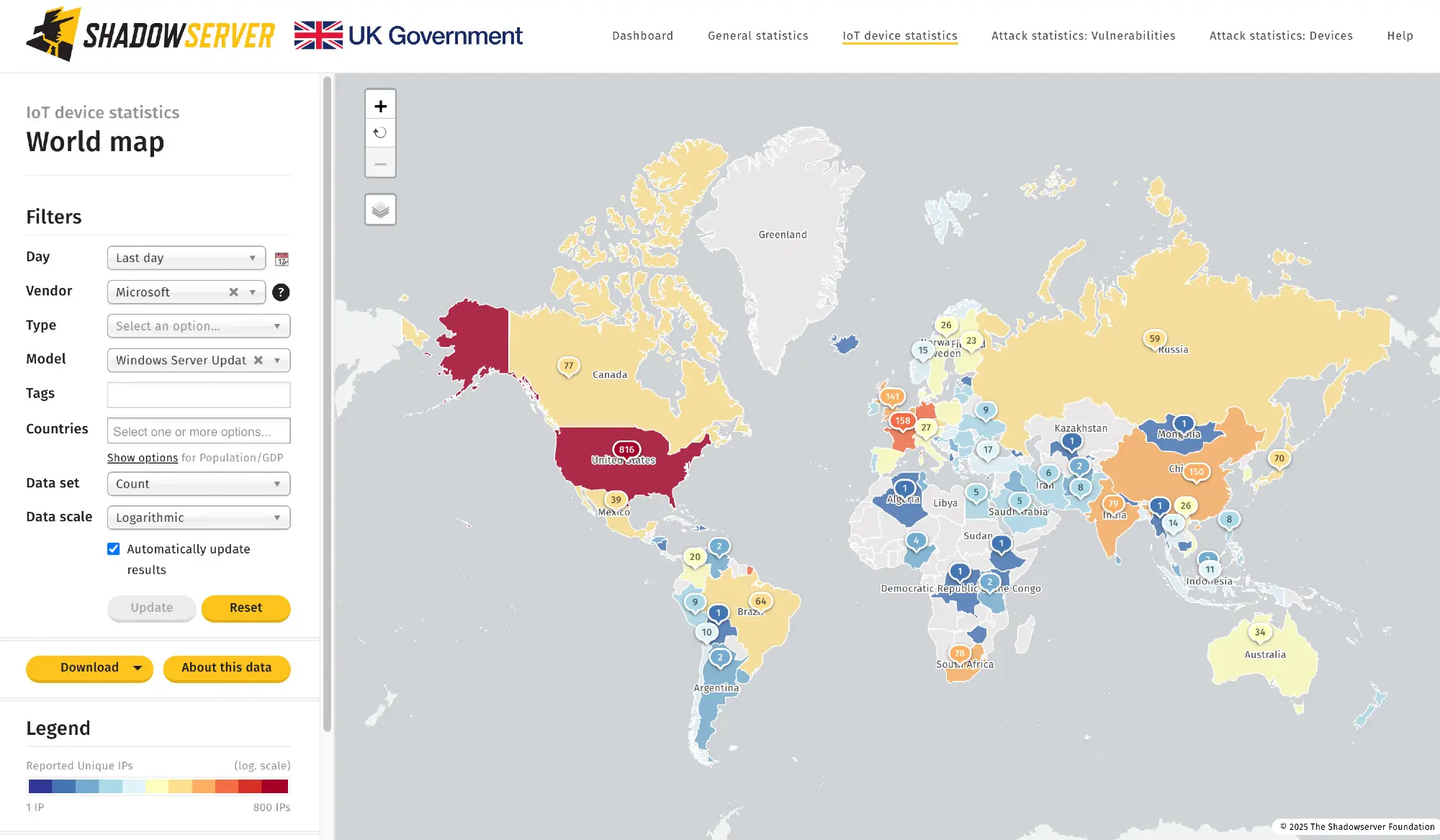
According to estimates by ShadowServer, at least 2,800 servers worldwide were vulnerable as of October 25, as shared in a post on Bluesky. The European epicenter is in France (158) and the United Kingdom (141).
Microsoft currently considers it ‘likely’ that the vulnerability will be exploited, despite reports that it has already happened. However, the warnings have not fallen on deaf ears: last Friday, Microsoft pushed an emergency patch to adequately resolve the security issue. The original update released on October 14 was not sufficient.
Emergency patch available
An update is available for the following Windows Server versions, with the corresponding update in parentheses:
- Windows Server 2025 (KB5070881)
- Windows Server, version 23H2 (KB5070879)
- Windows Server 2022 (KB5070884)
- Windows Server 2019 (KB5070883)
- Windows Server 2016 (KB5070882)
- Windows Server 2012 R2 (KB5070886)
- Windows Server 2012 (KB5070887)
If Microsoft’s advice to quickly install the update is not enough, various national security organizations recommend the same. Among others, the Dutch Cybersecurity Center urges updating WSUS to the latest version as soon as possible. This also protects you against another actively exploited SMB vulnerability in Windows.
